
CVE-2023-30846 : MICROSOFT TYPED-REST-CLIENT UP TO 1.7.3 INSUFFICIENTLY PROTECTED CREDENTIALS
Description typed-rest-client is a library for Node Rest and Http Clients with typings for use with TypeScript. Users of the

Description typed-rest-client is a library for Node Rest and Http Clients with typings for use with TypeScript. Users of the

What Is Security Misconfiguration? What Is Security Misconfiguration? Security misconfiguration refers to the failure to properly configure and maintain the

Have you ever wondered how important XML is? And how insecure it can be if XML is parsed in an
Prophaze 5G API Security Protecting Your Business in the New Era of Connectivity Prophaze offers 5G API security solutions with

How Prophaze Secured Two Indian airports from Layer 3-7 DDoS attacks ? On 8th April 2023 Anonymous Sudan launched an attack
Prophaze API Security AI-Powered Protection for Every API. Zero Compromise Prophaze API Security offers next-gen protection for your APIs with

Overview On-premises means that a business installs and controls its own software, hardware, or infrastructure within its physical space. Prophaze
Prophaze’s WAF-as-a-Service Elevate Your Web Application Security with Prophaze’s WAF Prophaze’s WAF-as-a-Service is a reliable and effective solution to secure

Description TP-Link Archer AX21 (AX1800) firmware versions before 1.1.4 Build 20230219 contained a command injection vulnerability in the country form

Description There is a logic error in io_uring’s implementation which can be used to trigger a use-after-free vulnerability leading to

Web Application Firewalls (WAF) have existed for quite some time to safeguard web applications by inspecting HTTP traffic. Traditionally, on-premises WAFs
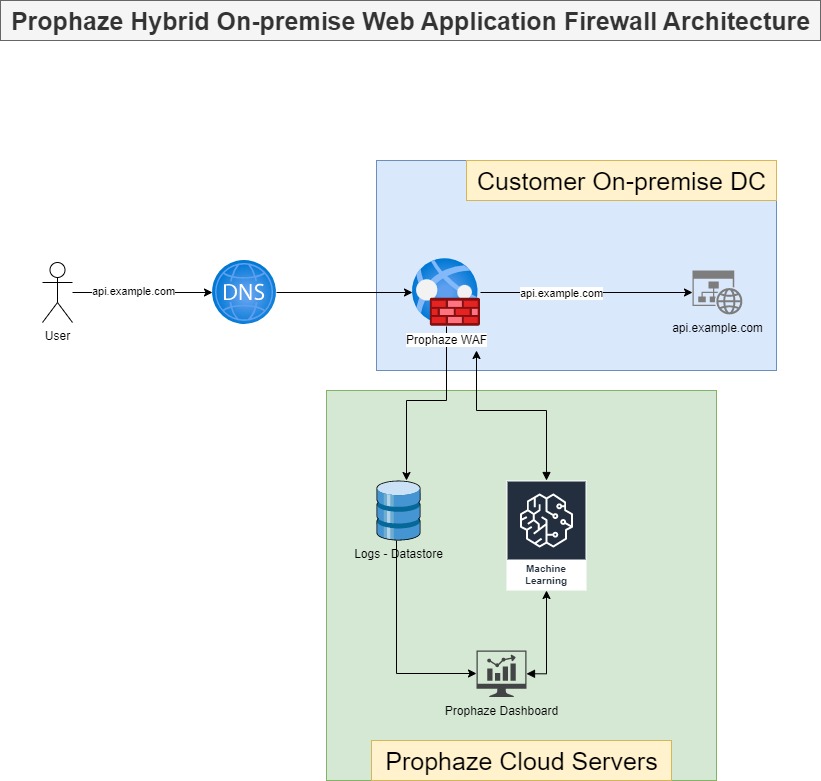
On-Premises WAF Prophaze WAF Supports On-Premises Prophaze WAF support on-premises deployment to ensure compliance with security in industries such as

Description authentik is an open-source Identity Provider focused on flexibility and versatility. Versions prior to 2022.11.4 and 2022.10.4 are vulnerable
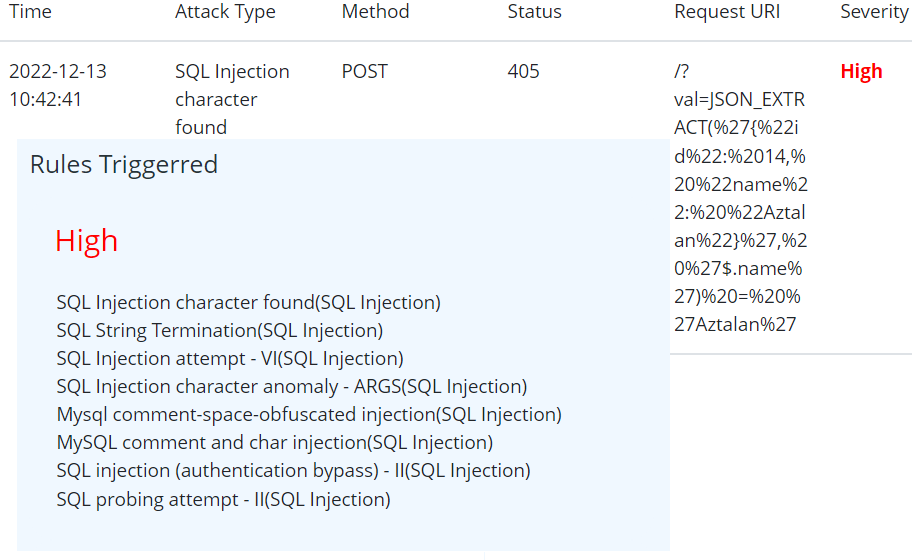
A New WAF Bypass hack has been identified by claroty team. This uses json based sql strings which is not conventionally been

Security For Examination Portals The education sector has also been impacted greatly by the digitalisation post-Covid pandemic. Services have been

Description Multiple Xiongmai NVR devices, including MBD6304T V4.02.R11.00000117.10001.131900.00000 and NBD6808T-PL V4.02.R11.C7431119.12001.130000.00000, allow authenticated users to execute arbitrary commands as root,

Description Vela is a Pipeline Automation (CI/CD) framework built on Linux container technology written in Golang. In Vela Server and

Description In Spring Security versions 5.5.6 and 5.6.3 and older unsupported versions, RegexRequestMatcher can easily be misconfigured to be bypassed

What Is Credential Stuffing? A cyberattack known as “credential stuffing” occurs when a cybercriminal gains access to user accounts at
What is REST API? REST is the acronym of Representational State Transfer (REST). It is an architectural style or pattern
What is Session Hijacking? Session Hijacking is the type of attack in which the attacker takes over or hijacks a

What is DNS and how does it work? DNS is the abbreviation for Domain Name System. The task of the

What is Content Security Policy (CSP)? Content Security Policy (CSP) is an additional layer of security on the HTTP browser

What is Swagger? Swagger is the way of defining the structure of APIs (Application Programming Interface). Swagger is specifically developed